In the modern era, where cybercrimes continue to rise steadily, the need to have solid and reliable methods of identity authentication of identities has never been more crucial, both to businesses and individuals. Knowledge-Based-Authentication (KBA) is a method that has existed long enough, but is not without its flaws. This is a review of KBA and what it is, the kinds of it available, how it works, its advantages and disadvantages (in a table format), the current trends and the future of this method.
A method of identity verification for a user that utilises information they are expected to know alone is known as Knowledge-Based-Authentication (KBA). As opposed to passwords that are easily weak, reused or stolen, KBA uses personal data or past information, such as the maiden name of your mother, the name of your first pet or even your previous address.
It is commonly used in other industries, such as finance, particularly in transactions that require high stakes or account recovery. KBA does not require expensive hardware, but it has been criticised for failing to offer sufficient security due to the increase in sophistication of cyber threats.
KBA comes in two main forms:
Based on predetermined security questions that the user must establish during the account setup process.
Examples:
“Maiden name of your mother?”
“What was the name of your first school?”
Pros: Simple and easy to use.
Disadvantages: Hackers may guess responses by using public information or any social engineering techniques.
Produces queries on the fly based on either a public or a private database.
Examples:
“In which of these addresses have you dwelt?”
“How much was your previous utility bill?”
Advantages: It is more difficult to predict, making it more secure than fixed KBA.
Disadvantages: Privacy issues, as it relies on third-party data.
There are usually the following steps in the Knowledge-Based-Authentication process:
The user begins by typing in the ID or username and password.
In case of a required verification, the system asks the user security questions.
The system compares the user responses with the retrieved or stored data.
In case the responses are similar, the user is allowed to access or finalise his /her transaction.
In the last ten years, Static Knowledge-Based-Authentication has become less popular. It is particularly susceptible to social engineering, in which hackers rely on publicly available information to make guesses. The social media sites have aggravated the issue because individuals tend to post personal information without their knowledge.
Dynamic KBA has become the new favourite among many organisations, particularly financial services organisations. A 2023 study by Jumio determined that 72 per cent of financial institutions have abandoned the concept of a static KBA and have migrated to dynamic KBA to fight fraud and data breaches.
There is an increasing number of companies that combine KBA with Multi-Factor Authentication (MFA). Dynamic KBA is usually combined with biometrics or hardware tokens to add an extra security advantage. A 2024 Hyperverge report documents that 85 per cent of companies now apply MFA, and most of them apply KBA in the process.
AI is transforming KBA. State-of-the-art fraud detection systems consider the reaction of users on the fly and indicate suspicious behavioural patterns. This renders the exploitation of personal data more difficult, even by attackers who possess part of it.
The use of third-party data by the Dynamic KBA has become an issue of privacy concern. Businesses are dealing with it by implementing zero-knowledge architectures, in which the sensitive data is encrypted and can be accessed by authorised parties only.
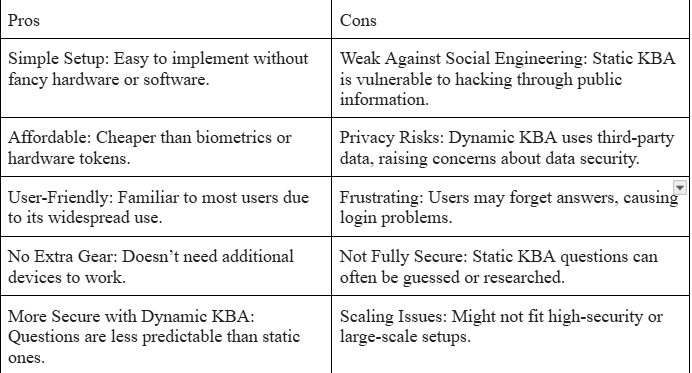
Privacy Risks: Dynamic KBA provides third-party data, which raises concerns about the security of the data.
Ease of use: It is easy to use because of its everyday use.
Irritating: The user can lose answers and have issues with logging in.
No Special Equipment: Does not require any extra equipment.
Not Fully Secure: Static KBA questions are sometimes easy to guess or research.
More Secure with Dynamic KBA: The questions are not as predictable as the static ones.
Scaling Problems: may not be suitable for large-scale or high-security environments.
The following are ways organisations can make the most out of KBA:
Go Dynamic: Dynamic KBA is used to ensure that questions are not predictable.
Use It with MFA: For greater security, make KBA use stronger means such as SMS codes or biometrics.
Encrypt Data: Make sure that all sensitive information in the KBA is encrypted.
Avoid Generic Question: It is essential to avoid questions that are based on publicly known information.
Provide Alternatives: Offer options, such as biometrics, to users who cannot remember their answers.
Biometric Authentication: Consider fingerprints, face scans, or voice recognition —high security and convenient.
Behavioural Biometrics: Tracks specific behavioural patterns, such as typing patterns or swipe gestures, for verification.
Hardware Tokens: Devices with one-time passwords (OTPs) are best suited for high-security applications.
Passwordless Authentication: Email-based magic links or device-based authentication, such as FIDO2 keys, are examples of passwordless authentication.
KBA is pressured to keep up with the more advanced cyber threats. As the previous KBA is becoming a relic, there is still potential in the dynamic KBA, although it remains subject to improvement, particularly with new technologies. The future of KBA includes:
AI Integration: AI-based fraud detection will increase the challenge of giving fake responses by attackers.
Improved Privacy Controls: Tighter controls and encryption will redefine the way data is processed.
Layered Security: Knowledge-Based-Authentication will remain part of the multilayer security systems.
Its role will also be reduced, but KBA will always remain helpful where more sophisticated approaches are not feasible.
Knowledge-Based-Authentication (KBA) has been key in ensuring the digital identity of many over the years, but its weaknesses have become more evident. Although dynamic KBA is more secure than its counterpart, static Knowledge-Based-Authentication, combining it with other sophisticated technologies like multi-factor authentication (MFA) could provide the most favourable security results. With the ever-changing nature of the digital world, the role of KBA is likely to be influenced by the emerging trends in cybersecurity and privacy laws. KYC Hub leads in knowledge-based authentication with advanced built-in features and algorithms. Get the best compliance system for your business by partnering with us.